Many Facets, One Point AT A GLANCE Life is not a destination, it is a journey, many major philosophers say. So is security, it appears. As with life, the circumstances surrounding security measures are dynamic. Situations c 'Security threats come from a variety of sources,' says Kim Fenrich, systems product marketing manager, ABB Inc. 'They range from internal accidents to virus and worm infiltrations and external attacks by malicious hackers. Historically, studies have indicated the majority of the incidents were internally generated, but that trend has rapidly shifted to non-directed, automated, externally generated attacks. Corporations must understand that incidents and attacks are possible, and implement security policies, procedures, and processes, in addition to hardware and software devices, to mitigate the risk associated with them.' Establishing effective safeguards for human-machine interfaces (HMIs), the components with which they interact, and the networks on which they reside require a multi-faceted, multi-leveled effort. That effort needs to focus on the 'people' side with policies and processes and on the 'technology' side with hardware and software measures. A balancing act 'Security is all about risk assessment,' says Roy Kok, director of HMI/SCADA product marketing, GE Fanuc Automation. 'You have to understand your vulnerabilities—and they are a moving target. As you add enhancements or introduce new products into your
Safeguarding data in automation and control systems boils down to risk assessment that emphasizes policies and procedures as much as technology.
hange, and automation and controls engineers concerned about security need to stay on top of those changes. Today, in an environment fraught with terrorism, computer viruses, litigation, and privacy issues, these words have seldom been truer.
Addressing security is a matter of balancing risk and needs. How much risk can an operation tolerate? At what cost? Open systems in a Microsoft Windows environment make information accessible and vulnerable even as that company and others work to build-in security and help people better cope with patches. In addition, proliferation of industrial Ethernet has placed net
works, systems, and HMIs at increased risk. In light of these realities, how should engineers respond?
Begin by identifying who, and what team, is considering security measures, recommends Andy Bedingfield, electrical engineer with Soltus, an engineering services company. 'Ask what security concerns and constraints have been built into the systems up until now,' says Bedingfield. 'And find out what other concerns about security the firm may have. Second, try to assess what the typical threats might be. A more automated environment has different concerns than a manual environment. Third, describe the consequences if a breach occurs. Then weigh costs vs. risks.'
'When we do a security assessment,' explains Marilyn Guhr, services marketing manager, Honeywell, 'we analyze and verify what's going on in a customer's process control networks, especially with open nodes. This would include the HMI operator interface. We provide a documented report of the vulnerabilities we have observed, along with recommendations and best practices guidance as to how to remove or mitigate the vulnerabilities. There is a level of risk associated with each vulnerability. The determination of how much risk is acceptable to the business is ultimately the responsibility of the customer.'
In some situations, security measures must be set up with caution. Kevin Staggs, control systems solution planner, Honeywell, recommends predefining what a system will do when an operator logs on. 'We ship systems
with sample log-on scripts that pre-configure the desktop, or pre-start the applications an operator is allowed to run. He isn't allowed to launch anything else.'In critical process HMIs, you don't want such things as screen savers automatically kicking in when the process operator is using the system,' warns Staggs. 'The operator always needs to have a view to the process. Even common practices such as a password lockout may create a situation where the operator can't view the process when he
needs to. In critical event situations, when adrenaline is flowing—if you can't remember a password because you're excited or confused—well, that's a situation you don't want. Since the operator's password may not be as secure as company security policies may recommend, the underlying operating system must be completely locked down to prevent unauthorized modification.'
Under other circumstances, connected systems need more protection. 'HMIs are very sophisticated today,' points out Rami Al-Ashqar, product manager, Bosch Rexroth Electric Drives and Controls. 'Because of all the things that HMIs can do, a facility needs to safeguard those operations. Without proper security, an unauthorized person can do significant damage. Engineering needs to work with IT to block those who should not access information while ensuring that those who should can access that data. IT departments can help. Use that expertise. It should be a cooperative effort.'
The importance of policy
The human factor is the weakest link in any activity. And security is no exception. First and foremost, a security plan must be formed and implemented. Establish a standard, a consistent methodology, implemented throughout the facility, even the company. And ensure every employee understands it.
Next, develop documents that define what needs to be done. Where are the holes? And how can they be plugged? Many common security problems are personnel related:
- Failure to implement and update v
IT departments are ahead of automation and control departments when it comes to security issues, continues Mody. 'Use your IT department's expertise; work with them to leverage their security knowledge.'
Finally, be aware that un intentional problems can be as big a security risk as intentional ones. 'The greatest vulnerability,' says Iconics' President Russ Agrusa, 'might be from an inadvertent attack by someone within your own facility who doesn't even know he's doing it. It could be a technician coming into your facility to do a repair. It could be the plant engineer who attends a conference with his laptop then plugs into the plant network. It could be an employee returning from a trip abroad. All of a sudden, your network is compromised. Policies need to have more to do with quarantining systems coming in or returning from the outside than with viruses and firewalls themselves.'
Get physical
Of course, security is more than policy. It embraces the physical as well as the procedural, and typically physical measures take the form of software and hardware. HMI issues center primarily on communications to and from the units. Nothing is totally effec
tive, but many measures provide deterrents. Most common are probably multi-level passwords.'But security goes beyond passwords on the desktop,' says Mark Prowten, senior product marketing manager for device networking products, Lantronix. 'It's moved down to the end devices, from the built-in computer on a robotic arm to the PDA that communicates to the device. A handheld PDA is wireless. Although wireless has become more secure with today's sophisticated encryption, the backbone of the networ
k is still hardwired. If anyone has access at that point, the information is at risk.'
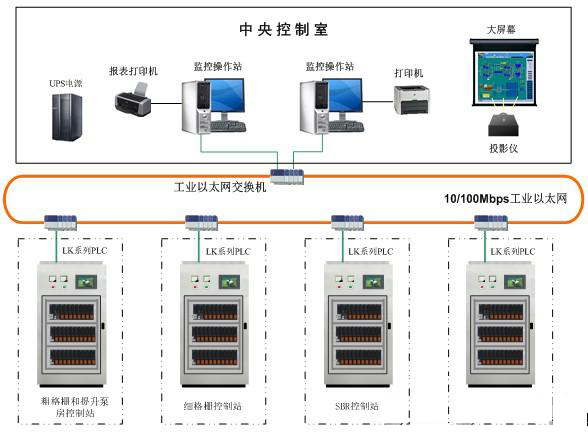
'Ethernet proliferation has put HMIs more at risk,' says Larry Komarek, automation product manager, Phoenix Contact. 'Open systems mean more risk. In the industrial world, these systems typically use managed and unmanaged switches. Unmanaged switches provide a solution, but they have no higher-level intelligence. They perform basic Ethernet switching at very low cost, but there is no security on an unmanaged switch. You plug in a device, and you have access. Managed switches help prevent that. They have additional intelligence to improve performance and add security. They also cost more.' (For more on managed switches, see the sidebar.)
On the hardware side, biometric devices can add to or replace passwords. Accuracy is high; error rate on a fingerprint reader is less than 0.1%. Setting up a system is simple, though it can be costly, in implementation and maintenance.
Many of these hardware measures for restricting access can be built into the HMI itself. Touchmonitors, for example, can be equipped with any of a number of biometric devices, which range from fingerprint and palm readers to card access systems. Such measures are especially common in the health care field, notes Mark Bolt, Elo TouchSystems' director of product management.
'HIPAA [Health Insurance Portability & Accountability Act] requirements in health care prohibit any equipment from being left unattended and in an
unlocked state if it has patient information on it,' he explains. 'As a result, personnel end up having to log on and off hundreds of times a day, a tedious and time-consuming task. With fingerprint access, a person touches a biometrics sensor right on the monitor and is recognized and logged in immediately.'If need be, HMI and associated networks and devices can also be physically restricted in a control room where access is allowed only by badge or other clearance device. Such measures must
be combined with policies that define who may enter and outline what action an operator should take if an unauthorized entry occurs.
Putting it all together
Technical advances for addressing security are being made everyday. However, no single solution or technology fits the needs of all organizations and applications.
'Having too much security—if there is such a thing,' says ABB's Fenrich, 'can restrict access to information and data to those with authorization, and create unnecessary cost. However, not enough security puts operating profits and people at risk. It is important to balance the cost of security measures with the potential cost of the event occurring. As a rule of thumb, plants should apply security measures that are proportional in cost to the value of data, risk, and probability associated with a security incident, and the potential consequences of the incident. To do so, plant personnel must understand the variables that contribute to the security risk.'
'Complete ownership of a project or system, end to end, can help mitigate security problems,' concurs Soltus' Bedingfield. 'You can't assume someone else is going to take care of a problem.'
'It's an education process,' adds GE Fanuc's Kok. 'Any company, to be successful in security, needs to create policies in house. They need to dedicate people to it. It can't be a half-hearted effort. Security needs to be everyone's job. Everyone needs to have security on his mind.'
And for good reason. '9/
11 ended our sense of security,' says Lantronix' Prowten. 'We like to think we're taking care of things, but we don't realize how much we're leaving open.'For more information on the companies mentioned in this article, visit their Web sites listed below:
www.abb.com
www.boschrexroth-us.com
www.elotouch.com
www.gefanuc.com
www.honeywell.com/ps
www.iconics.com
www.lantronix.com
www.phoenixcon.com
www.soltus.com
www.wonderware.com
One key
to managing HMI security in an Ethernet-network-dominant environment is the managed switch. Switches must be addressed on three levels, explains Phoenix Contact's Larry Komarek.
- Accessing ports/connections.
Access to the ports of switches is needed so that a system can be operable. However, control of those ports on multiple levels is critical. 'You want a spare port for maintenance to use for plugging in a laptop to do diagnostics,' says Komarek. 'But you don't want that port 'on' all the time for anyone to use. You want to be able to turn it on and off to prevent misuse. You can do this with password protection and switch management.'
A port can also be set to check a lookup list of approved addresses. 'If your equipment is not on the approved list, you don't get access,' says Komarek. 'For example, a new line is going in while other lines continue to run. Startup personnel need access to certain areas, but they are not permanent employees and should not be free to access everything. So you can approve the device they're using for access on a port-by-port basis.'
In response to wrong address, the port can be shut down completely if an unapproved address is detected. In those instances, the port may be configured to require either a manual reset, or it can be configured to block unapproved devices but respond if an approved device is subsequently plugged in.- Managing switch parameters.
Measures can also be taken to prevent someone from accessing the switch itself and changing - Managing switch parameters.
Virtual networks, or VLANs isolate traffic. Says Komarek, 'VLANs can isolate portions of a network as completely as if the cables were cut and separate network interface cards were put in. In this way, certain personnel can be given access to one section of a network, but not to others, or to the whole network.'
HMIs can be physically secured in a control room where access is allowed only by badge or other clearance device.(photo courtesy ABB)
Biometrics technologies, such as fingerprint validation, can improve HMI/SCADA security and convenience by replace passwords.(photo courtesy GE Fanuc)
Fingerprint access (bottom left) or magnetic card swipe readers (bottom right) incorporated into an HMI monitor (top)can speed login procedures,ensure authentication, and eliminate the need to remember and change passwords.(photo courtesy Elo TouchSystems)
SecureBox provides an end-to-end solution for networking-enabling HMI products and ensures that information within devices can be securely accessed and transmitted over the network or internet. This device is certified by the National Institute of Standards and technology (NIST) for implementation of 128-256 bit AES encryption. (Photo courtesy Lantronix)
Defining multilevel password security gives operators access only to the specific network areas they need. Here, “Jo
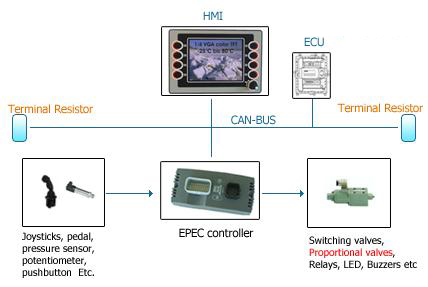
Encryption devices help secure data communications from end devices to HMI monitors. (Illustration courtesy of Lantronix)